KVM Access
Beyond Remote Desktop
Gain physical control and process data On-Premise with Bifrost KVM Access – Secure and reliable Remote Access to your Critical Infrastructure without exposing any endpoints to the Internet.
Remote Access as it should be
Rethink Remote
Desktop
In the past, Remote Access Software and VPN connections were the go-to solutions for Remote Access to both IT and OT equipment. They were considered secure and sufficient for accessing devices in isolated networks. However, times have changed.
With the increasing threat of cybercrime and the fusion of IT and OT, these tools are no longer suitable for secure Remote Access to critical infrastructure equipment. They lack the necessary security measures to protect against advanced threats and cannot reach specialized devices in offline scenarios or before the operating system is successfully booted. This creates significant vulnerabilities in critical systems and jeopardizes business continuity.
Imagine if you could establish remote access to air-gapped equipment without exposing it to the internet and ensuring no data leaves your network perimeter.
Eliminate attack surfaces and ensure Business Continuity
Grant Endpoint Access
Keep Endpoints Air-gapped
Boost User Experience
Support GPC Devices

Reach All Your GPC Devices
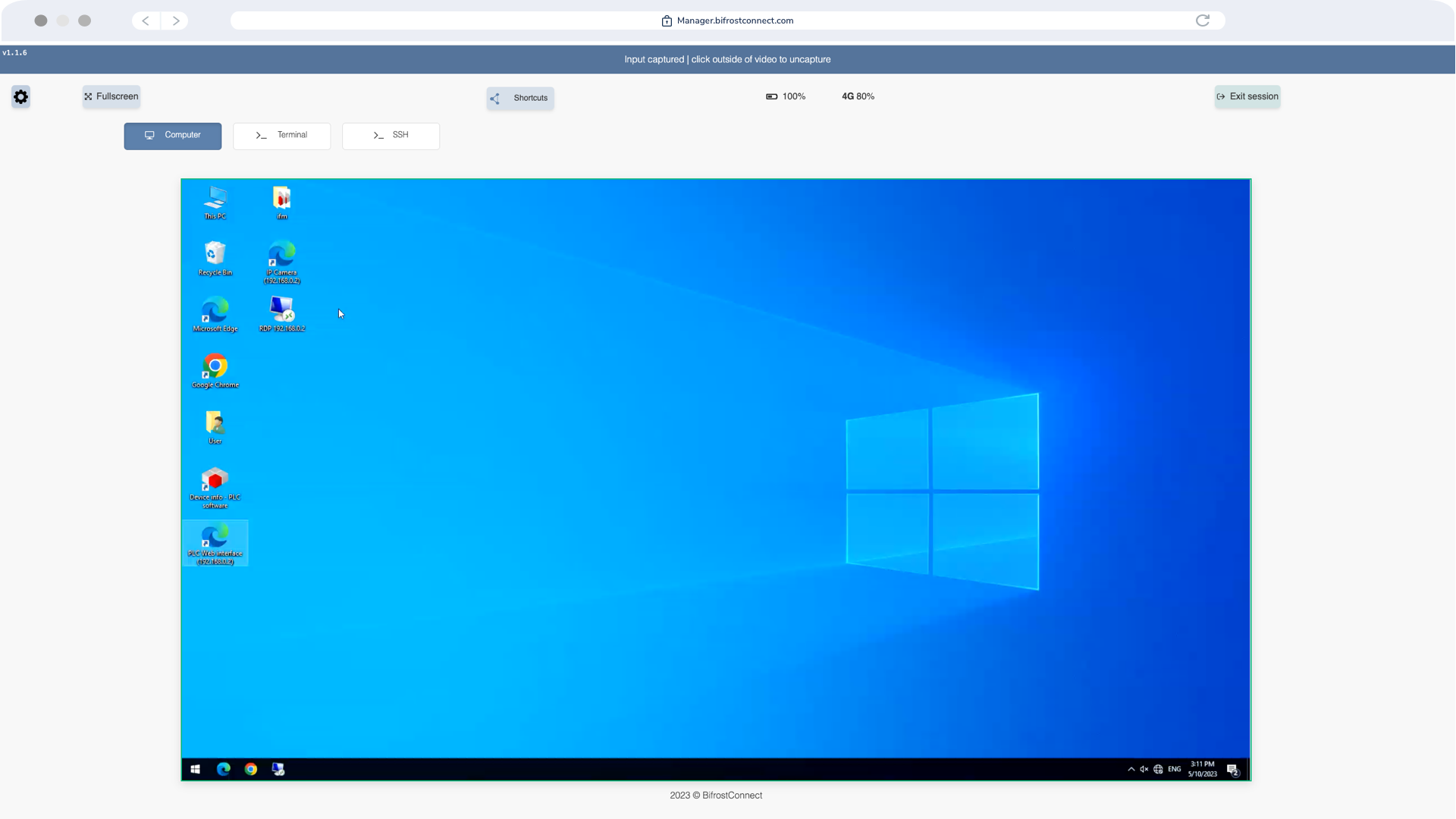
Say goodbye to complicated remote access solutions. With BifrostConnect KVM Access, providing Remote Access to authorized IT specialists has never been easier. Simply connect the Bifrost Unit to your General-purpose Computing Device and watch as remote operators control your equipment as if they were in front of it.
KVM Access behaves like a second screen, keyboard, and mouse, providing instant and secure access to your IT equipment. There's no need for software installations, and
once authenticated, your equipment is virtually teleported into your trusted specialists' hands within seconds.
Get instant hands-on:
- Computers & Servers
- Industrial PCs
- Mobile & Tablets
Plug & Fix
No training necessary. Just connect the Bifrost Unit to the device and let the remote specialist fix the problem.
Endpoint

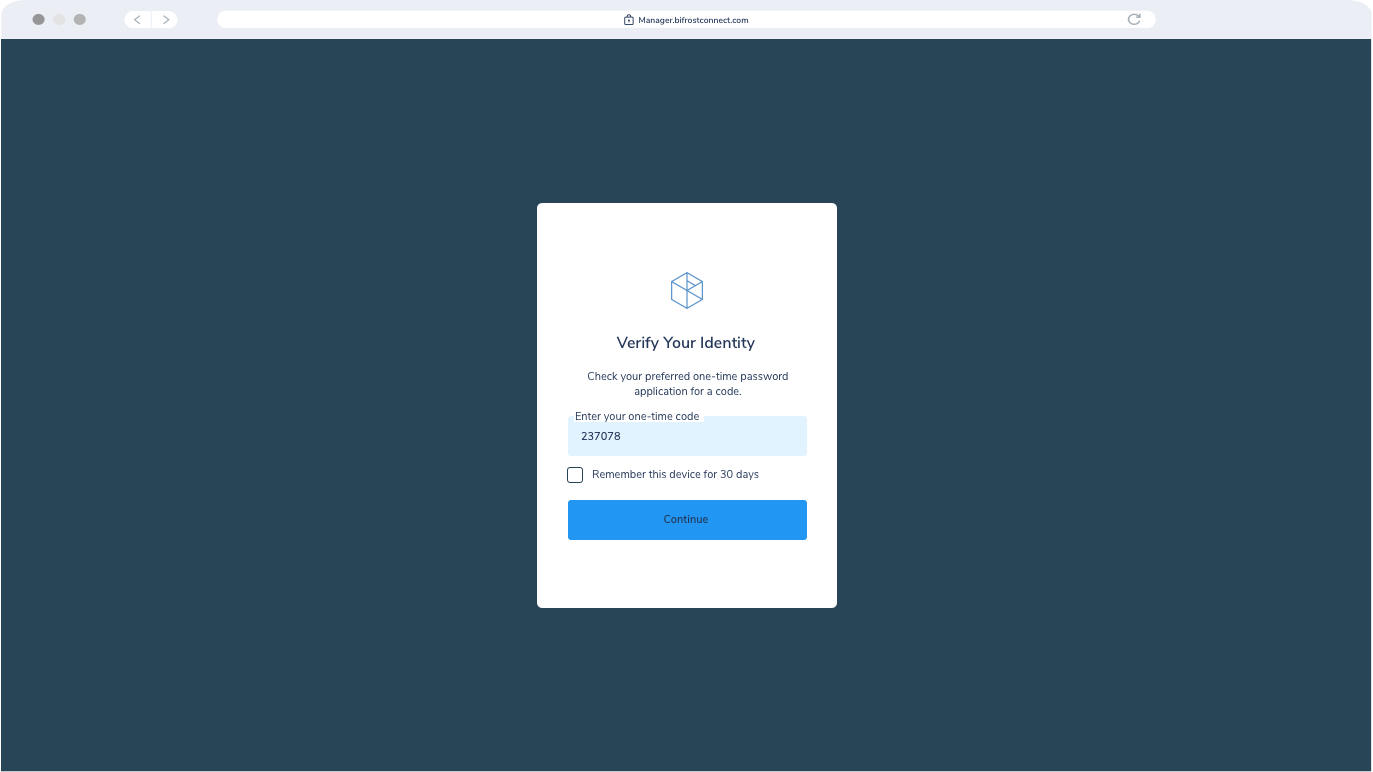
MFA Interface
KVM Interface
Session Terminated
When is KVM Access the perfect match?
If you want to gain physical control of the endpoint and process data onpremise, this solution is for you.
Commissioning
Support & Maintenance
Field Service Support
Incident Response
How it works
With BifrostConnect KVM Access, you can get in front of the problem instantly without accessing the company's network or exposing the endpoint to the internet. Our solution provides secure remote access to your air-gapped environment without compromising your security perimeter.
BifrostConnect isolates endpoints from the internet, making them invisible to unauthorized access while ensuring no data leaves your network perimeter. This minimizes attack surfaces and reduces the risk of cyber attacks.
A Unified Remote Access Platform
Together as a suite, the BifrostConnect Solution gives you unmatched flexibility in tailoring your Zero Trust Access and scaling up your existing setup.
Secure
- Air-gapped Remote Access
- Out-of-band LTE connectivity
- End-to-End Encryption
- Transitory Session Data
- Multi-Factor Authentication
- SAML integration
- Access Management
- Audit Logging
Versatile
- Support all platforms
- IP Tunnel Sessions
- KVM Sessions
- Terminal/Serial Sessions
- SSH Sessions
- File Transfers
- BOOT/BIOS Access
- Portable/On-demand
Plug and Play
- Offline Remote access
- Hassle-free implementation
- No software installs
- No network configuration
- Out-of-the-box commissioning
- No on-site configuration
- Easy to use
- Hosted Private Infrastructure