Easy. Safe. Versatile.
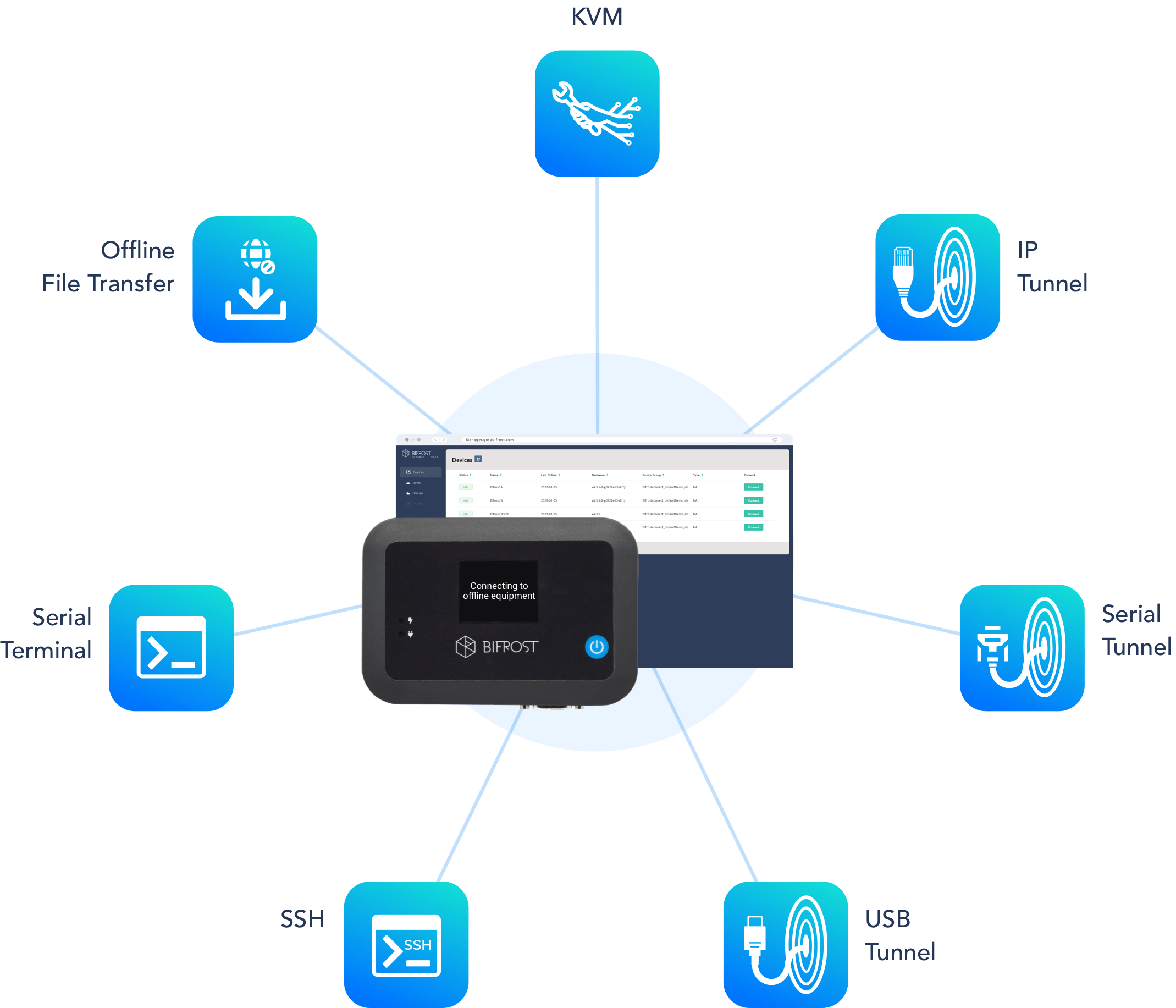
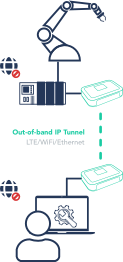
Whether you need KVM, Terminal, or IP-based access, the BifrostConnect Solution allows you to reach any device Out-of-band without exposing any endpoints to the Internet.
Remote Access as it should be




All-in-one Access.
Across all devices.
USED FOR
- Commissioning
- Field Service
- Support
- Operations
- Engineering Projects
- Data Extraction
- Endpoint Updates
- Incident Response
Explore our most popular tools
Zero software installs. Zero internet exposure. Zero networks compromised.
IP Tunnel
KVM Access

It’s NOT a Box.
It’s a Bridge.
In Nordic mythology, Bifrost is the name of the bridge between the
world of the gods and the world of us humans.
Today, Bifrost is a highly secure remote access solution that bridges
the gap between the connected equipment and your IT Specialist,
regardless of the distance between them.
Designed and manufactured in Scandinavia, BifrostConnect is built
on nordic values of innovation, quality, and trust.
How do you want to authenticate?
Secure third-party access or continuous connectivity – we've got your back.
Choose your preferred method of authentication

Attended Access

Unattended Access
BifrostConnect Zero Trust principles
Grant access on a "need-to-know" basis, based on granular policies, without needing a VPN or remote access software.
Isolated Application Access:
Inside-Out Connections:
Just-in-Time Access:


A Unified Remote Access Platform
Together as a suite, the BifrostConnect Solution gives you unmatched flexibility in tailoring your Zero Trust Access and scaling up your existing setup.
Secure
- Air-gapped Remote Access
- Out-of-band LTE connectivity
- End-to-End Encryption
- Transitory Session Data
- Multi-Factor Authentication
- SAML integration
- Access Management
- Audit Logging
Versatile
- Support all platforms
- IP Tunnel Sessions
- KVM Sessions
- Terminal/Serial Sessions
- SSH Sessions
- File Transfers
- BOOT/BIOS Access
- Portable/On-demand
Plug and Play
- Offline Remote access
- Hassle-free implementation
- No software installs
- No network configuration
- Out-of-the-box commissioning
- No on-site configuration
- Easy to use
- Hosted Private Infrastructure
Your Manager, Your Rules
Access Management
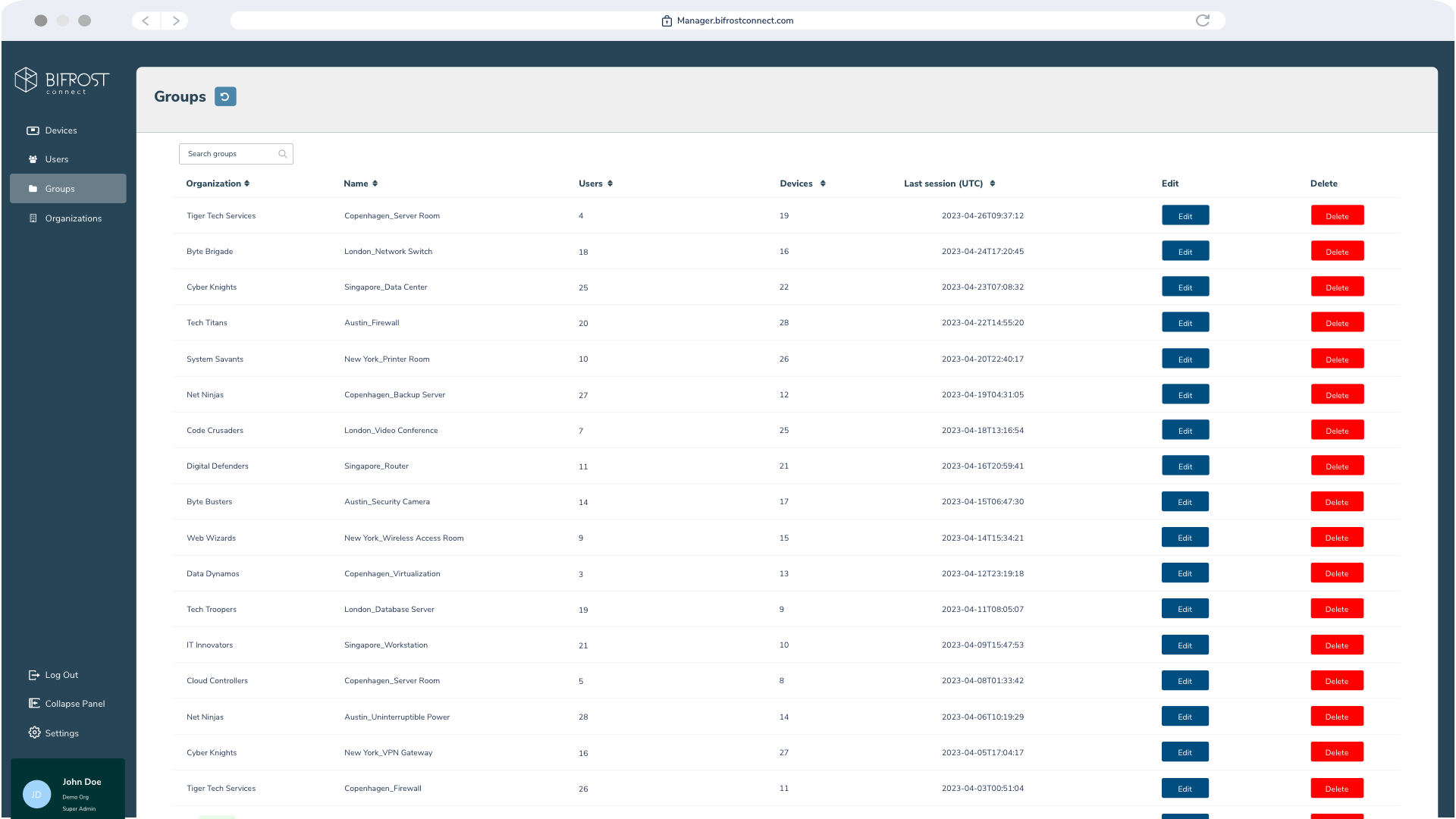
Ensure hyper-focused access to endpoints and applications by applying Granular policies at the application and user level and least-privileged access to internal and third-party users.
Mission Control
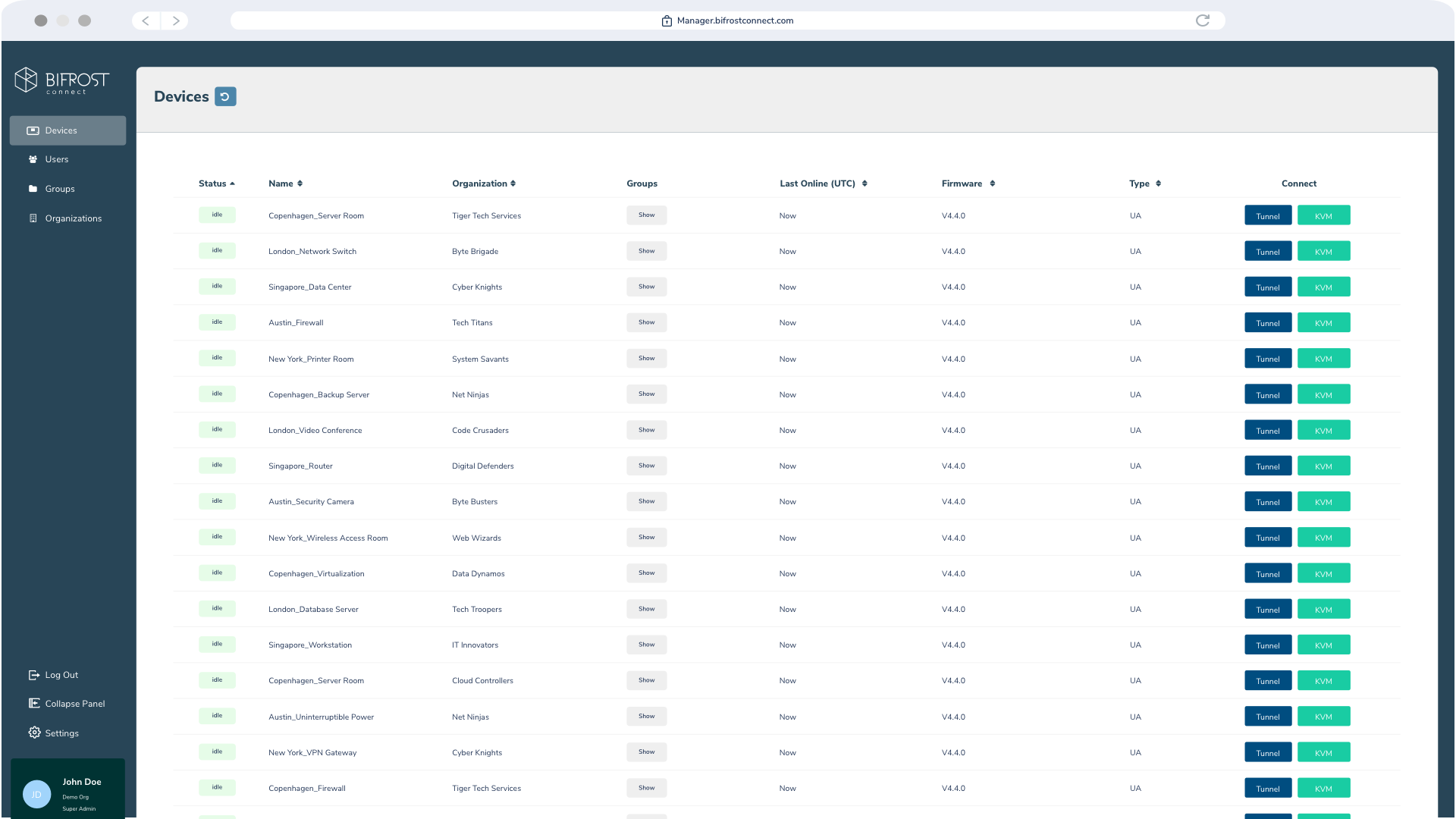
Establish end-to-end encrypted KVM, Terminal, or Tunnel access to authorized endpoints on demand.
Audit Log
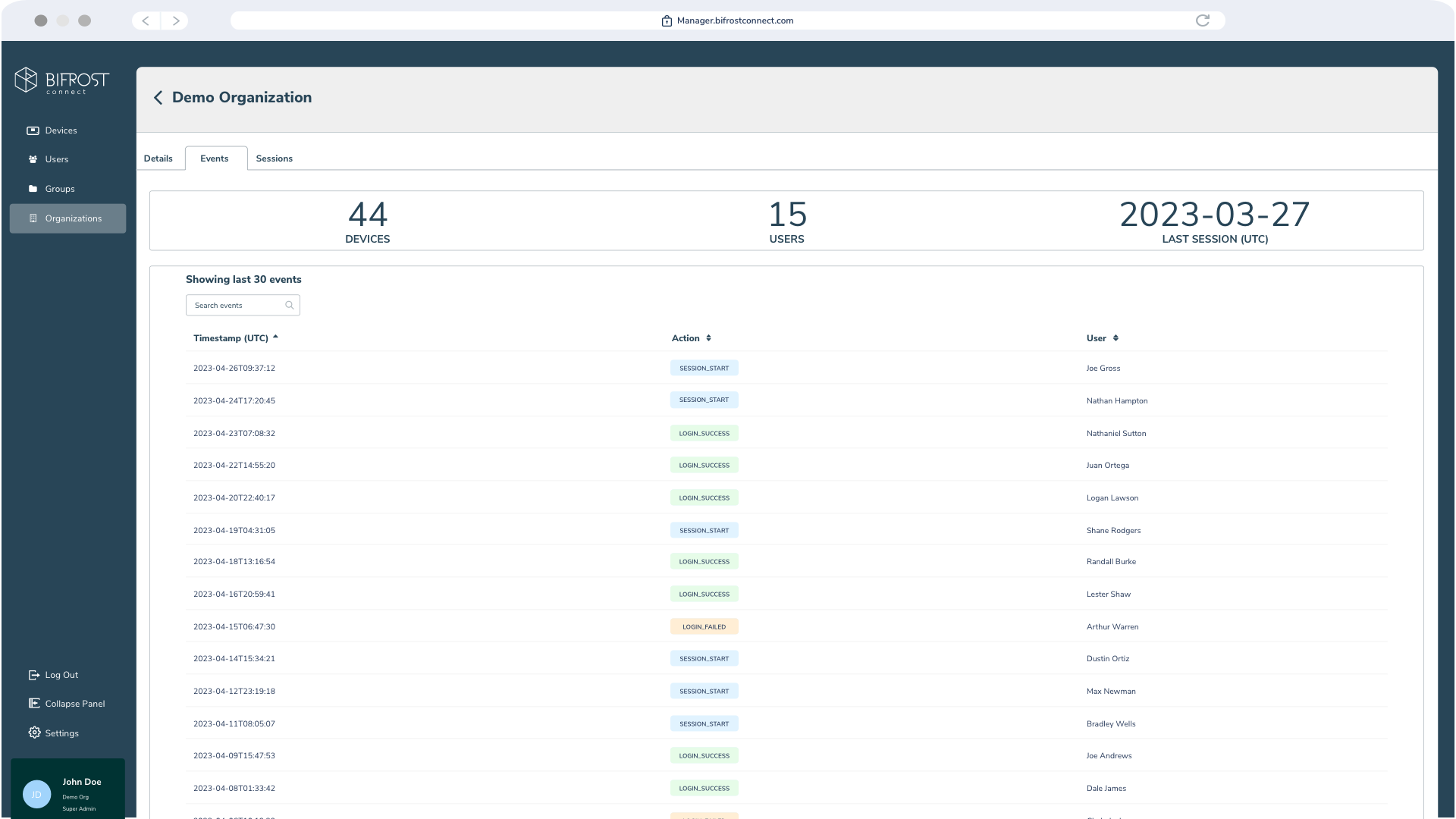
Monitor and document activities across your organization. Streamline your reporting with an extended audit trail that integrates directly with your preferred SIEM solution.
Patented technology
Our patented technology helps eliminate human error and saves time and money while simplifying your transition to Zero
Trust.
Enjoy instant connectivity and the highest level of security
without worrying about vulnerable third-party access or static
IP addresses.
Eliminate attack surfaces in your critical infrastructure and
ensure business continuity in your operations.

Securing Remote 3rd Party Access in Critical Infrastructure
Watch our webinar and enhance your understanding of securing third-party access.