Serial Tunnel
Next-gen Serial Connectivity
Establish Serial connections on-demand without exposing endpoints to unauthorized users or the Internet.
RS232 Meets Enterprise Security
In the OT world, Serial communication has set the standard for nearly three decades. Both legacy and cutting-edge systems hinge on this protocol for configuration, troubleshooting, and data extraction. To modernize and keep pace with today's needs, interfaces like Serial-to-Ethernet were crafted to bring devices into the realm of Ethernet-based networks.
But, diving into these ready-made solutions isn't without its pitfalls.
Implementation
Challenge:
Bifrost Serial Tunnel:
Security
Challenge:
Bifrost Serial Tunnel:
Access Management
Challenge:
Bifrost Serial Tunnel:
Zero Trust
Serial Connectivity
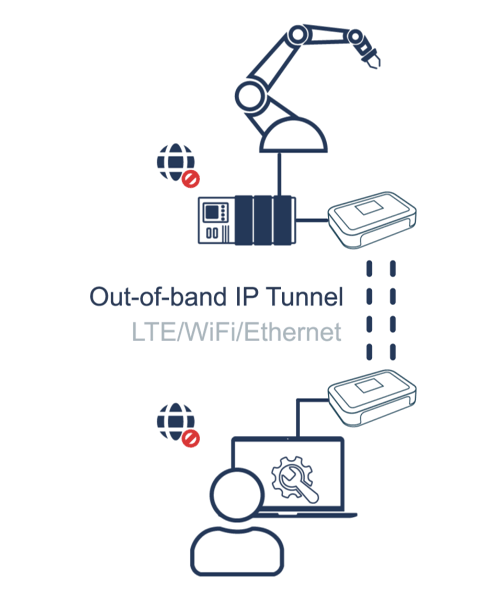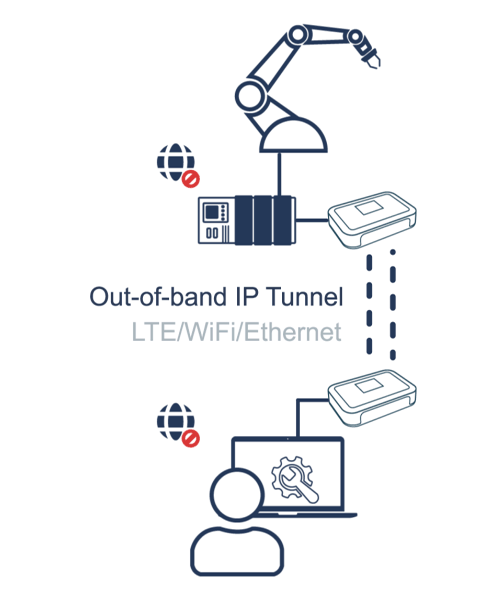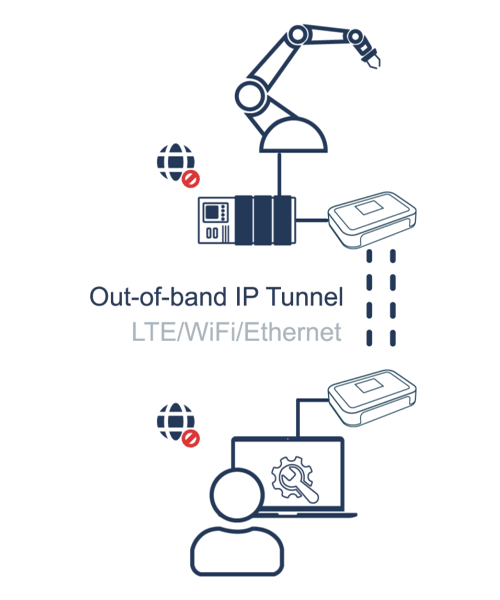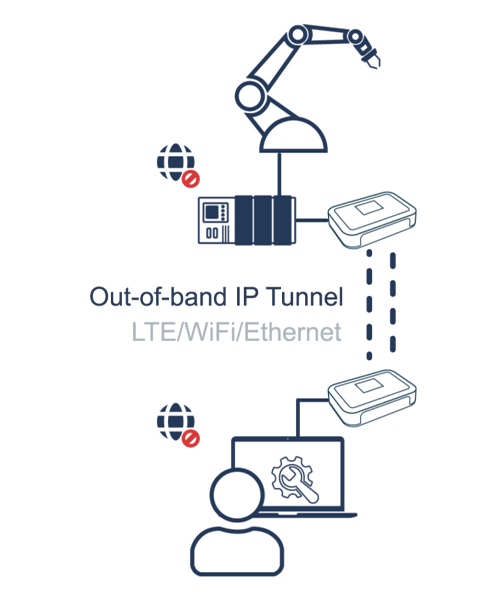
A Bifrost Serial Tunnel facilitates a secure, encrypted session between two Bifrost Units. These tunnel sessions are initiated just in time, safeguarding sensitive information by ensuring session data is transient and never stored on servers.
Bifrost Units can connect using standard LAN or Wi-Fi or a dedicated 4G connection. Notably, a Bifrost Unit won't expose the endpoints to the Internet while in a Serial Tunnel Session.
Building on the principles of Least Privilege, only Users or Admins with the appropriate permissions can initiate a Serial Tunnel Session.
When paired with Bifrost KVM Access, authorized users can initiate clientless Remote Access concurrently with setting up a Serial Tunnel Session. This feature allows the privileged user and the Bifrost Units to be in separate locations during the Remote Access sessions.

Grant Endpoint Access
Minimize Attack Surfaces

Boost User Experience
Deploy Clientless Access
Remote Serial Communication as it should be
Grant Endpoint Access
Minimize Attack Surfaces

Boost User Experience
Deploy Clientless Access
Establish Next-gen Serial Tunnels
Hasslefree Point-to-Point Access without extensive setup or expert knowledge.
Endpoint

MFA Interface
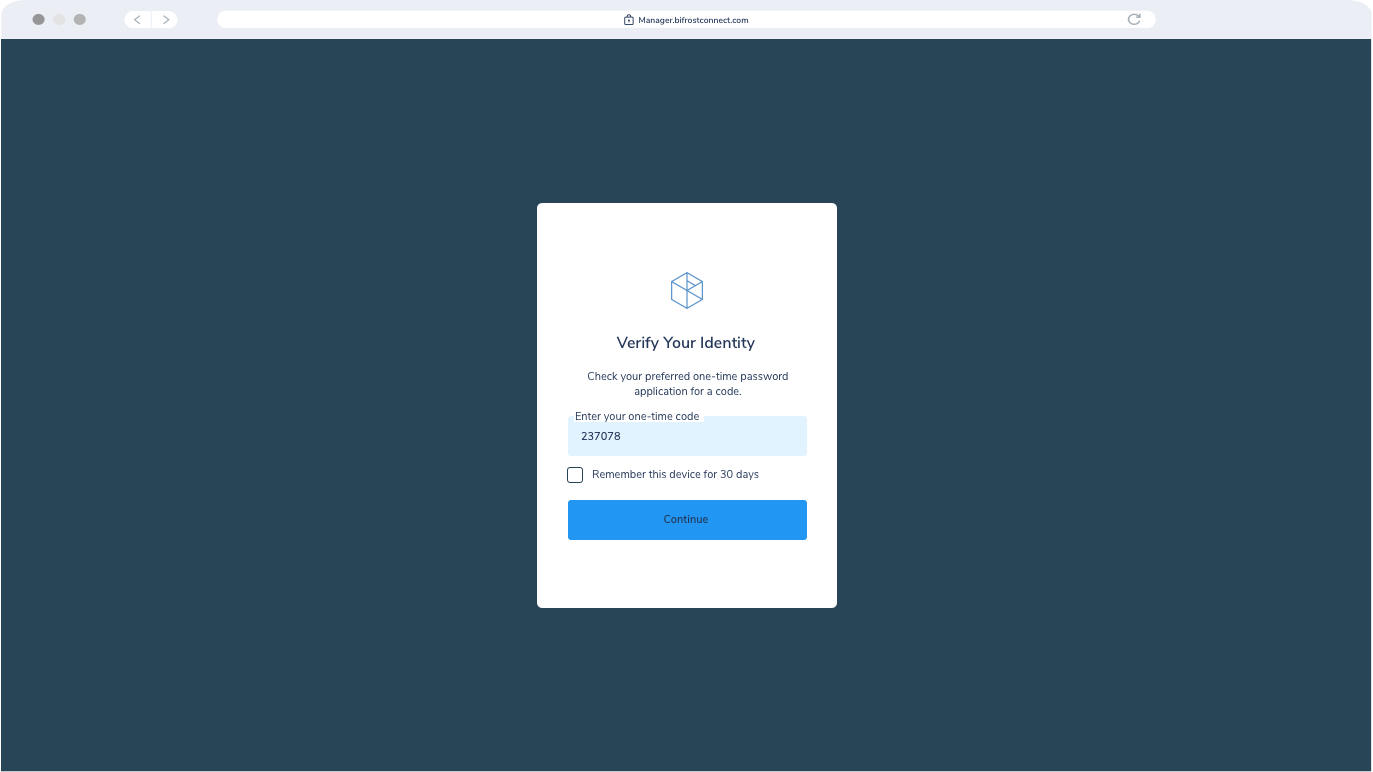
The Authenticator service validates the Users’ right to access and configure the specific Bifrost Unit.
Serial Tunnel Interface
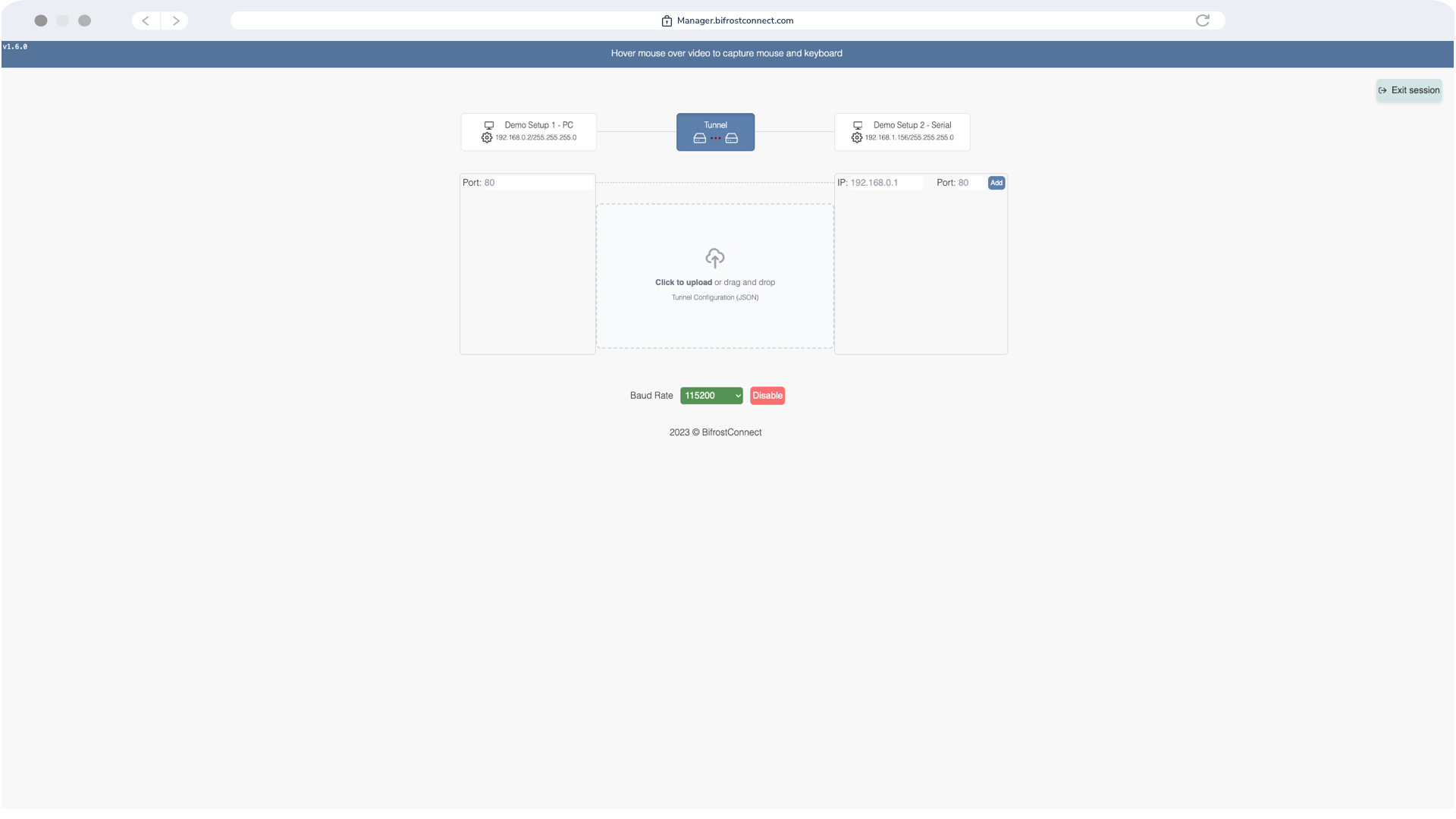
Session Terminated
Optional: Disconnect the Bifrost Unit
Try our
Serial Tunnel Product Tour
Discover how easy and secure it is to establish a remote serial communication via our serial tunnel solution

Zero Trust
Serial Connectivity
A Bifrost Serial Tunnel facilitates a secure, encrypted session between two Bifrost Units. These tunnel sessions are initiated just in time, safeguarding sensitive information by ensuring session data is transient and never stored on servers.
Bifrost Units can connect using standard LAN or Wi-Fi or a dedicated 4G connection. Notably, a Bifrost Unit won't expose the endpoints to the Internet while in a Serial Tunnel Session.
Building on the principles of Least Privilege, only Users or Admins with the appropriate permissions can initiate a Serial Tunnel Session.
When paired with Bifrost KVM Access, authorized users can initiate clientless Remote Access concurrently with setting up a Serial Tunnel Session*. This feature allows the privileged user and the Bifrost Units to be in separate locations during the Remote Access sessions.
Discover How You Can Establish Zero Trust Access to Your Equipment
Get in touch with one of our experts today.How it works
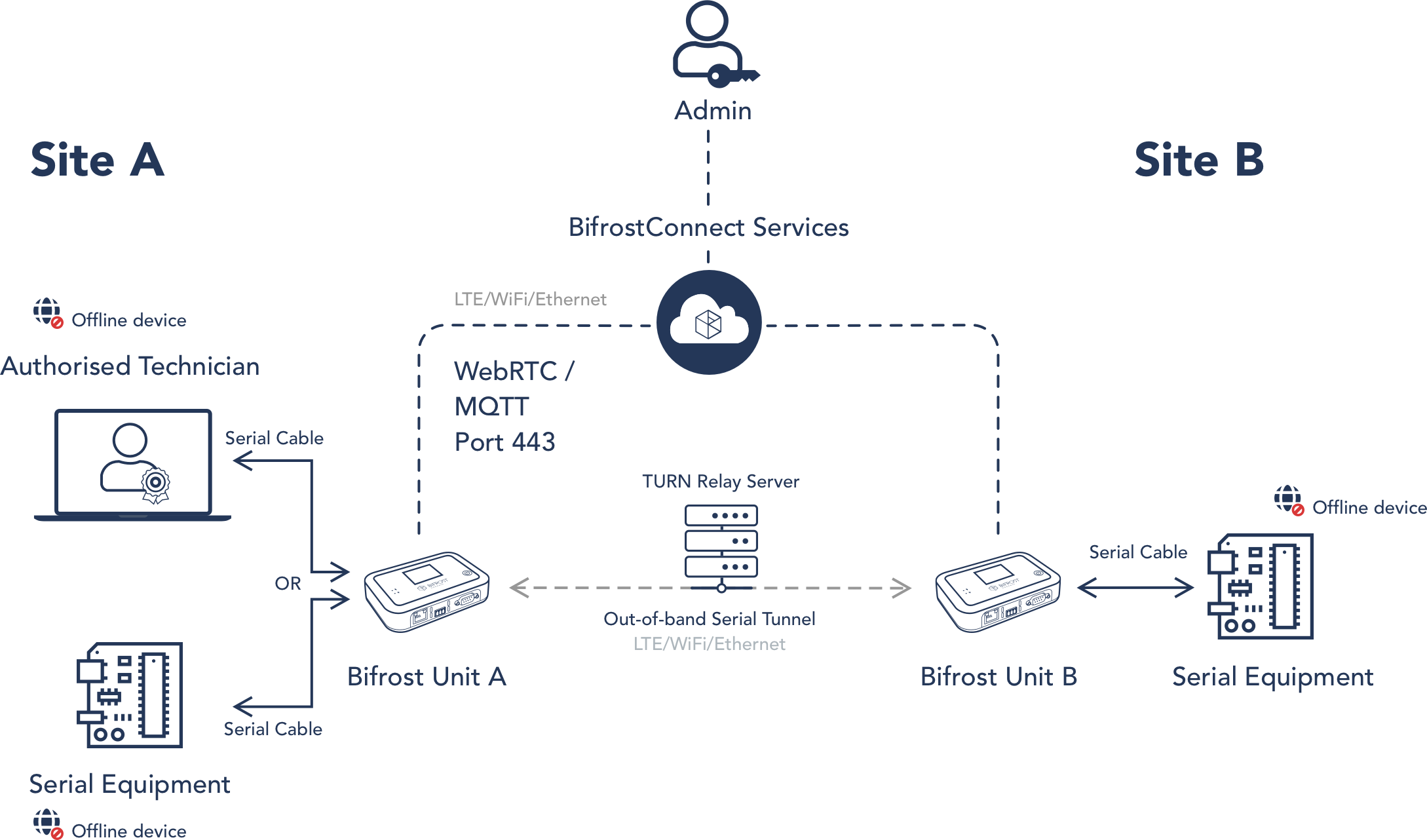
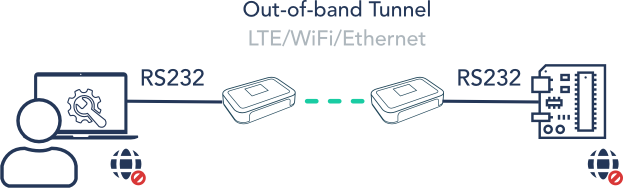
Site A: Attach the Bifrost Unit to the computer you intend to use for operating the serial equipment at Site B or to the serial equipment you plan to connect with the equipment at Site B directly.
Site B: Link the Bifrost Unit to the Serial Equipment.
Once set up and activated, devices linked to the Bifrost Units at both Site A and Site B will essentially be bridged by a virtual serial cable without borders. Authorized users at Site A can then engage with the equipment, bypassing the need for vulnerable login details that could be jeopardized post-session.
For enhanced security, devices at both locations can remain offline, paving the way for Air-gapped Remote Access.
A Unified Remote Access Platform
Together as a suite, the BifrostConnect Solution gives you unmatched flexibility in tailoring your Zero Trust Access and scaling up your existing setup.
Secure
- Air-gapped Remote Access
- Out-of-band LTE connectivity
- End-to-End Encryption
- Transitory Session Data
- Multi-Factor Authentication
- SAML integration
- Access Management
- Audit Logging
Versatile
- Support all platforms
- IP Tunnel Sessions
- KVM Sessions
- Terminal/Serial Sessions
- SSH Sessions
- File Transfers
- BOOT/BIOS Access
- Portable/On-demand
Plug and Play
- Offline Remote access
- Hassle-free implementation
- No software installs
- No network configuration
- Out-of-the-box commissioning
- No on-site configuration
- Easy to use
- Hosted Private Infrastructure
Explore related resources
Zero Trust Access Test
February 15, 2020Is your organization equipped with the necessary tools to ensure your perimeter security remains intact during remote access?
Solution Brief: IP Tunnel
May 1, 2023How to take critical OT infrastructure offline while boosting remote access capabilities through air-gapped IP communication.
Discover BifrostConnect
May 1, 2023Zero Trust Access boosts remote work, expands market reach, saves resources, and prolongs technology lifespan.
Remote IP Communication
as it used to be
Conventional firewalls, VPNs, and Remote Access Software provide a considerable attack surface.
Externally exposed endpoints are vulnerable to cyber threats, allowing attackers to see and exploit them.
VPNs, in particular, can give attackers easy access to sensitive data by putting users directly on the network.
Traditional network security approaches often fail to prevent free lateral movement, leaving your network vulnerable to cyber attacks.
Legacy devices not designed with contemporary security standards are susceptible to cyber threats.
Connecting Legacy equipment to a VPN could inadvertently expose the entire network to attack.