Offline File Transfer
A Secure Passage for Essential Data
Enable file transfers to offline devices without exposing endpoints or networks to unauthorized users or the Internet.
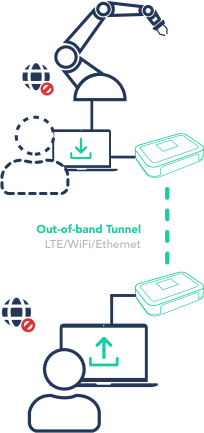
Master offline data exchanges
Many crucial devices are deliberately disconnected from the Internet for protective measures against cyber-attacks. Coupled with restrictions on VPN usage to avoid the risk of lateral movement within closed networks, this can complicate routine tasks like software updates, log file extraction, and data gathering for business intelligence.
Bifrost Offline File Transfer is here to simplify that landscape. Dive in and discover how you can maintain top-tier security while enhancing efficiency and data-driven insights.
Remote File Transfer as it should be

Update Offline Endpoints

Minimize Attack Surfaces

Extract Offline Data
Support USB Devices

No Exposure. Pure Transfer.
With Bifrost Offline File Transfer, you can move critical files between endpoints without exposing them to unauthorized users or internet risks. Our unique approach ensures all data is transitory and is never stored on servers, while your endpoints are physically safeguarded from IP communication during the transfer process. This eliminates the threat of lateral movement on closed networks.
Control with SFTP
Leverage your preferred SFTP client to manage and secure files during your transfer sessions. Safeguard sensitive information with password protection, ensuring data accessibility solely to authorized users post successful transfers.
Automate with Scripts
Take control over the transfer of data between your endpoints with ease. By deploying scripts that integrate with your Bifrost Units, you can enforce and predefine what data is available for file transfer and push transfers, all within your desired frequency.
Keep it simple. Keep it safe.
Implement swiftly and effortlessly without requiring extensive setup or complex configurations,
leveraging the tools you already know and trust.
Endpoint

MFA Interface
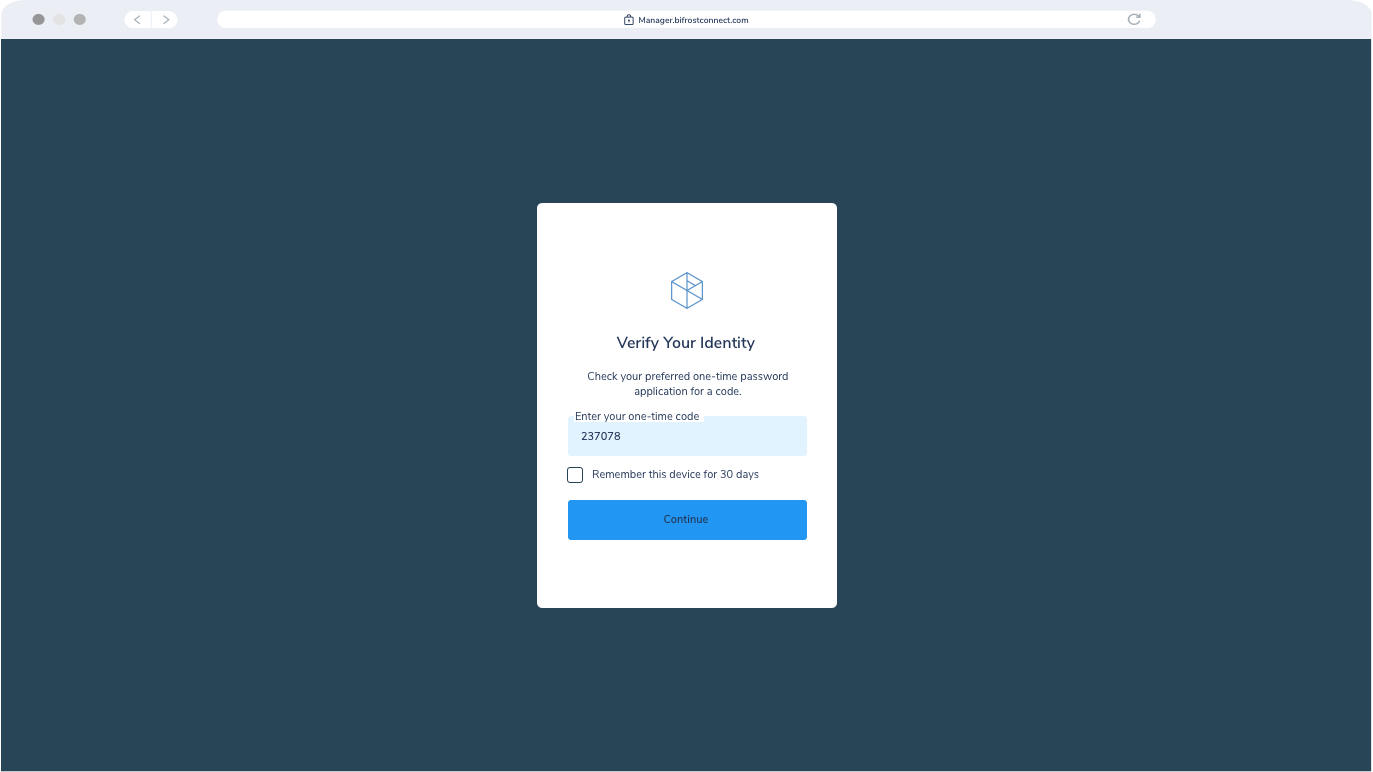
The Authenticator service validates the Users’ right to access and configure the specific Bifrost Unit.
File Transfer Interface
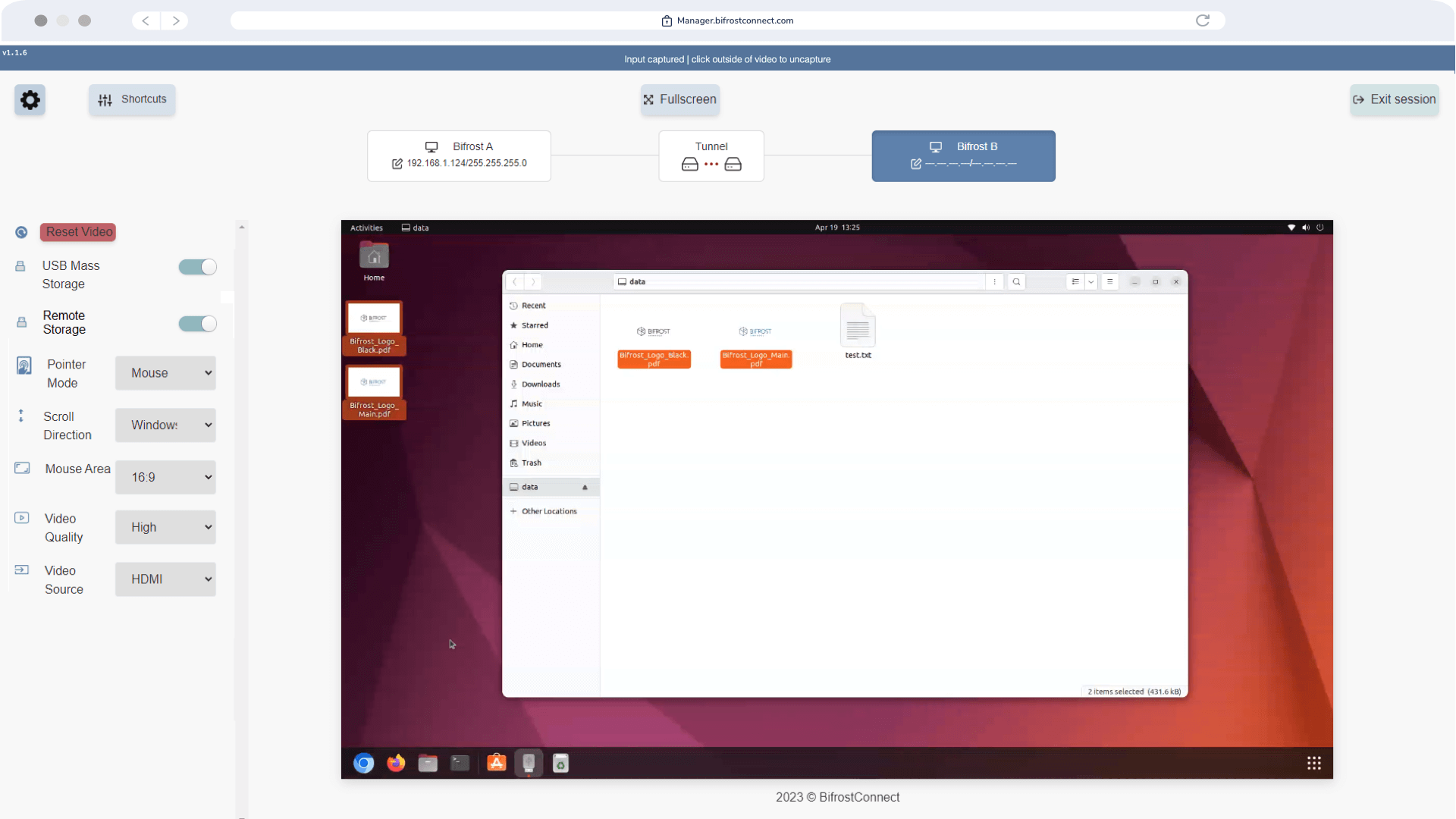
Option: In a pull scenario, the Privileged User moves files from the endpoint to the Bifrost Unit.
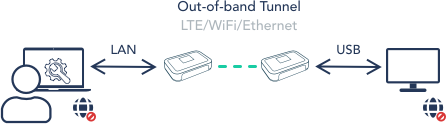
Privileged users can further leverage KVM Access to transfer these files between the Unit and the endpoint.
Session Terminated
Optional: Disconnect the Bifrost Unit
Discover How You Can Establish Zero Trust Access to Your Equipment
Get in touch with one of our experts today.Offline Scenarios

Keep endpoints offline while:
How it works
When implementing Offline File Transfer, Bifrost Units are placed in:
Site A: Place the Bifrost Unit to establish SFTP communication with the Bifrost Unit connected to the endpoint at Site B.
Site B: Set up the Bifrost Unit you wish to use as a local storage intermediary for transferring files to and from the endpoint.
A Bifrost Unit has 6GB internal storage available.
Once initiated, endpoints linked to the Bifrost Unit at Site A will form a closed network with the Bifrost Unit at Site B. Users with access to the device at Site A can then use an SFTP client to transfer files to and from the Bifrost Unit at Site B, given they possess valid session credentials. Privileged users can also utilize KVM Access to transfer these files between the Unit and the endpoint. For enhanced security, devices at both sites can remain offline.
A Unified Remote Access Platform
Together as a suite, the BifrostConnect Solution gives you unmatched flexibility in tailoring your Zero Trust Access and scaling up your existing setup.
Secure
- Air-gapped Remote Access
- Out-of-band LTE connectivity
- End-to-End Encryption
- Transitory Session Data
- Multi-Factor Authentication
- SAML integration
- Access Management
- Audit Logging
Versatile
- Support all platforms
- IP Tunnel Sessions
- KVM Sessions
- Terminal/Serial Sessions
- SSH Sessions
- File Transfers
- BOOT/BIOS Access
- Portable/On-demand
Plug and Play
- Offline Remote access
- Hassle-free implementation
- No software installs
- No network configuration
- Out-of-the-box commissioning
- No on-site configuration
- Easy to use
- Hosted Private Infrastructure
Explore related resources
Zero Trust Access Test
February 15, 2020Is your organization equipped with the necessary tools to ensure your perimeter security remains intact during remote access?
Solution Brief: IP Tunnel
May 1, 2023How to take critical OT infrastructure offline while boosting remote access capabilities through air-gapped IP communication.
Discover BifrostConnect
May 1, 2023Zero Trust Access boosts remote work, expands market reach, saves resources, and prolongs technology lifespan.


